LET’S TALK ABOUT - NETWORK FORENSICS
LET’S TALK ABOUT - NETWORK FORENSICS
BASIC CONCEPT
Network forensics is a sub-branch of digital forensics relating to the
monitoring and analysis of computer network traffic for the purposes of
information gathering, legal evidence, or intrusion detection. Unlike other
areas of digital forensics, network investigations deal with volatile and
dynamic information. Network traffic is transmitted and then lost, so network
forensics is often a pro-active investigation.
Network forensics generally has two uses. The first, relating to
security, involves monitoring a network for anomalous traffic and identifying
intrusions. An attacker might be able to erase all log files on a compromised
host; network-based evidence might therefore be the only evidence available for
forensic analysis. The second form relates to law enforcement. In this case
analysis of captured network traffic can include tasks such as reassembling
transferred files, searching for keywords and parsing human communication such
as emails or chat sessions.
Two systems are commonly used to collect network data, they are:
-
brute force method "catch it as
you can", and
-
Intelligent method "stop look
listen" method
GENERAL ASPECTS ABOUT
Network forensics is a comparatively new field of forensic science. The
growing popularity of the Internet in homes means that computing has become
network-centric and data is now available outside of disk-based digital
evidence. Network forensics can be performed as a standalone investigation or
alongside a computer forensics analysis (where it is often used to reveal links
between digital devices or reconstruct how a crime was committed).
Another concept: the capture, recording, and analysis of network events
in order to discover the source of security attacks or other problem incidents
Compared to computer forensics, where evidence is usually preserved on
disk, network data is more volatile and unpredictable. Investigators often only
have material to examine if packet filters, firewalls, and intrusion detection
systems were set up to anticipate breaches of security.
Systems used to collect network data for forensics use usually come in
two forms:
1-
"Catch-it-as-you-can" –
This is where all packets passing through a certain traffic point are captured
and written to storage with analysis being done subsequently in batch mode.
This approach requires large amounts of storage
2-
"Stop, look and listen" –
This is where each packet is analyzed in a rudimentary way in memory and only
certain information saved for future analysis. This approach requires a faster
processor to keep up with incoming traffic
TYPES OF NETWORK FORENSIC
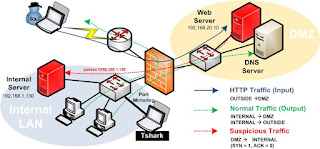
ETHERNET
Applying forensic methods on the Ethernet layer is done by eavesdropping
bit streams with tools called monitoring tools or sniffers. The most common
tool on this layer is Wireshark (formerly known as Ethereal) and tcpdump where
tcpdump works mostly on unix-like operating systems. These tools collect all
data on this layer and allows the user to filter for different events. With
these tools, website pages, email attachments, and other network traffic can be
reconstructed only if they are transmitted or received unencrypted. An
advantage of collecting this data is that it is directly connected to a host.
If, for example the IP address or the MAC address of a host at a certain time
is known, all data sent to or from this IP or MAC address can be filtered.
To establish the connection between IP and MAC address, it is useful to
take a closer look at auxiliary network protocols. The Address Resolution
Protocol (ARP) tables list the MAC addresses with the corresponding IP
addresses.
To collect data on this layer, the network interface card (NIC) of a
host can be put into "promiscuous mode". In so doing, all traffic
will be passed to the CPU, not only the traffic meant for the host.
However, if an intruder or attacker is aware that his connection might
be eavesdropped, he might use encryption to secure his connection. It is almost
impossible nowadays to break encryption but the fact that a suspect's
connection to another host is encrypted all the time might indicate that the
other host is an accomplice of the suspect.
TCP/IP
On the network layer the Internet Protocol (IP) is responsible for
directing the packets generated by TCP through the network by adding source and
destination information which can be interpreted by routers all over the
network (a common Firewall on a local LAN; in Linux you can use TCPDUMP).
Cellular digital packet networks, like GPRS, use similar protocols like IP, so
the methods described for IP work with them as well.
For the correct routing, every intermediate router must have a routing table
to know where to send the packet next. These routing tables are one of the best
sources of information if investigating a digital crime and trying to track
down an attacker. To do this, it is necessary to follow the packets of the
attacker, reverse the sending route and find the computer the packet came from
(i.e., the attacker).
THE INTERNET
The internet can be a rich source of digital evidence including web
browsing, email, newsgroup, synchronous chat and peer-to-peer traffic. For
example, web server logs can be used to show when (or if) a suspect accessed
information related to criminal activity. Email accounts can often contain
useful evidence; but email headers are easily faked and, so, network forensics
may be used to prove the exact origin of incriminating material. Network
forensics can also be used in order to find out who is using a particular
computer by extracting user account information from the network traffic.
WIRELESS FORENSICS
Wireless forensics is a sub-discipline of network forensics. The main
goal of wireless forensics is to provide the methodology and tools required to
collect and analyze (wireless) network traffic that can be presented as valid
digital evidence in a court of law. The evidence collected can correspond to
plain data or, with the broad usage of Voice-over-IP (VoIP) technologies,
especially over wireless, can include voice conversations.
Analysis of wireless network traffic is similar to that on wired
networks, however there may be the added consideration of wireless security
measures.
LET ME KNOW YOUR COMMENTS





Comments
Post a Comment